In an era that is referred to as digital transformation and where networking is the key determining factor of business success or failure, means that security is not an option. With emerging new risks, corporations need to use only the best ways to secure their valuable information, networks, and image. Network security software comprises a range of products and services that protect the networks from intruders, theft of vital data, viruses, and other internet threats.
The consequences are higher than in any previous point; businesses are at greater risk of ransomware, phishing scams, and APT. Excellent network security programs both protect against external threats and maintain business operations, adherence to standards, and client confidence.
This blog post discusses the top 15 network security solutions, the features involved, how and why to choose one, and why AI network security is essential for companies. From a small business to a large enterprise, this guide will assist you in the best decision-making regarding your online security.
What Is Network Security Solutions?
Network protection solutions may be described as the professional practices, measures, and technologies that are employed in order to safeguard a computer network in aspects such as its usage, information content, and physical structure. It is the methodical process of warping off cyber threats, hacking , data piracy & e-commerce security. The role of network security is multi-faceted:
- Protection: Protects information against loss due to another person’s unauthorized access.
- Prevention: Prevents any malware, ransomware, and other malicious processes that are normally seen on a computer.
- Compliance: It helps the business to follow strict rules of data protection such as GDPR and HIPAA.
- Trust Building: This creates confidence among the customers and the stakeholders of the company.
- Business Continuity: little or no disruption of service is experienced during the operation of the organization especially when experiencing cyber attacks
In the age of globalization and integration, networking provides a level of protection as a shield to innovation in organizations. Network security solution is not only a defence function, but also an enabler of business and digital trust.
Key Features of the Best Network Security Software
- Advanced Threat Detection: employs AI/ML to detect real-time threats together with their countermeasures at a high level of complexity.
- End-to-End Encryption: This facilitates the transfer of data between the networks without being intercepted.
- Multi-Layered Protection: A firewall is integrated with an IPS and antivirus for optimal protection from different kinds of threats.
- User Access Control: Adopting sound accreditation means using multifactor authentication since this helps in minimizing intrusions.
- Cloud Security Integration: It works well with multi-cloud including hybrid cloud environments by offering efficient protection.
- Scalability: Scales for business needs, protecting business’s growing networks and devices.
Top 15 Best Network Security Solutions
1. Palo Alto NGFWs
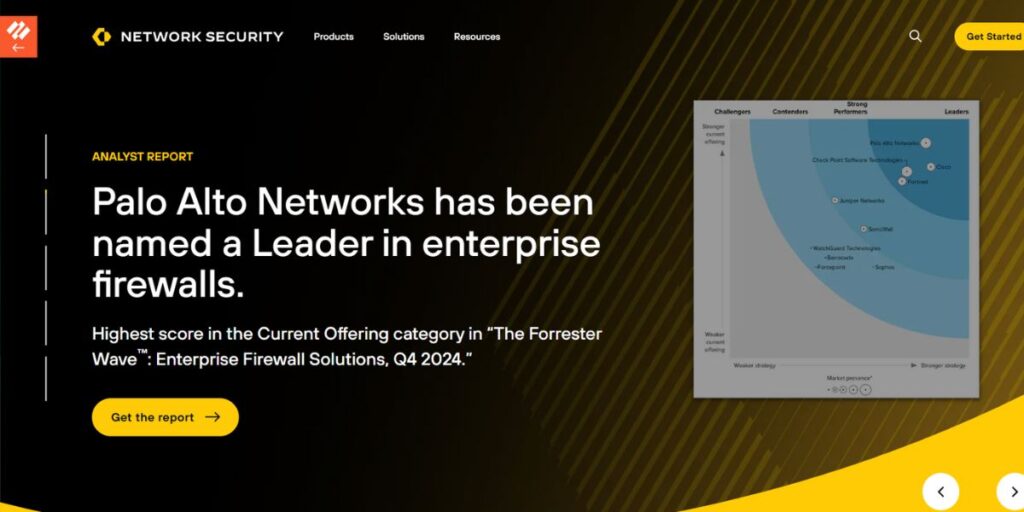
Palo Alto NGFWs enable one to have full visibility and control over network traffic. They employ sophisticated deep packet inspection where the suppliers are not only able to identify and prevent nasty viruses such as malware, ransomware and phishing attacks but also identify them.
They are synced with threat intelligence, particularly cloud, which confirms updates on nascent risks. These firewalls are also application-based and hence provide the necessary control over an application rather than depending on port or IP identification.
Key Features
- The solution also features deep packet inspection of potentially threatening flows and the incorporation of artificial intelligence.
- Application-specific firewalling with the resolution for enabling selective access.
Pros
- Advanced threat detection
- Granular application control
- Scalable performance
Cons
- Expensive for small businesses
- Requires skilled administrators
- Complex configuration
Price: Contact the vendor for pricing.
2. Zscaler’s SASE platform
Zscaler’s SASE Network Security Solution provides cloud security to the traditional network security by incorporating services such as SWGs, cloud firewalls, and DLPs. It provides authorized access to applications from anywhere in the world without any interruption. These network security solutions help ensure that remote users and devices are continuously protected, without compromising on performance.
The network infrastructure of zero-trust simplifies access rights to reduce security threats that may be faced by the organization. The company’s solution operates in real-time and is powered by artificial intelligence to protect growing remote and hybrid workforces at scale.
Key Features
- Single complex of web filters, firewalls and DLP systems.
- Zero Trust Architecture which characterizes the access control and minimizes the attainable points of infiltration.
- Real-time analytics for scalability and security for AI monitoring.
Pros
- Secure remote access
- Cloud-native architecture
- Real-time threat protection
Cons
- Bandwidth dependency
- High learning curve
- Limited customization
Price: Based on usage; contact sales for details.
3. Cisco Talos
Talos is a threat intelligence technology that targets to detect, analyze, contain and neutralize threats in any network-connected organization. Backed up by one of the largest commercial security research teams, it offers threat warnings and proactive countermeasures.
However, when connected to other Cisco security platforms, Talos provides total and preventive protection solutions. Its threat research enables organisations to avoid getting into the wrong side of the law by cyber criminals and also enables organisations to reduce their loss of time.
Key Features
- Threat intelligence offers global analysis by specialised internal researchers.
- Implementing threat detection and threat control in Cisco’s ecosystem to occur automatically.
- Data for prevention and timely response to security threats.
Pros
- Industry-leading threat intelligence
- Real-time updates
- Community-driven insights
Cons
- Requires Cisco ecosystem
- Limited to threat analysis
- Not user-friendly for non-technical staff
Price: Part of Cisco security solutions.
4. Fortinet FortiGate

There are currently no other NGFWs that offer intrusion prevention together with antivirus and web content filtering such as Fortinet’s FortiGate. It uses machine learning for threat identification and prevention with tight accuracy. This is easily deployable and manageable across the company because it is centralized.
SD-WAN integration with FortiGate provides a solution to maintain both security and efficient design for distributed businesses. Due to its cheap price and its high durability, it is ideal for small businesses as well as large ones.
Key Features
- Intrusion prevention system, Antivirus, Firewall, Web Access Control.
- Documentation of machine learning threat detection method for high accuracy.
- An integration of SD-WAN for secure as well as optimized connection.
Pros
- High-performance NGFW
- A broad range of features
- Cost-effective for SMBs
Cons
- Complex initial setup
- Limited support for third-party apps
- Interface can be clunky
Price: Starts around $400; varies by model.
5. CrowdStrike Falcon
Falcon CrowdStrike is an endpoint safeguard that embraces artificial intelligence in intelligent threat detection while also having superior endpoint tracking. The ligament of this agent is lightweight hence its ability to constantly scan the endpoints for any irregularities without much affecting the performance.
Speakers identify the so-called Threat Graph synthesizing big data and machine learning algorithms to visualize and forecast threats to the Network security solution. The relative real-time alarms and the swift response to threats are fundamental to mitigate the consequences of cyber intrusions.
Key Features
- Small-sized agent designed for endpoint monitoring with low effect on the endpoint’s performance.
- Presenting threat mapping applying big data, analytics, and machine learning.
- Alerts in real-time and quick actions are required to counter the malicious actions.
Pros
- Cloud-native endpoint security tool.
- Quick deployment
- Proactive threat hunting
Cons
- High subscription cost
- Dependency on Internet connectivity
- Limited on-premise options
Price: Starts at $8.99/user/month.
6. Buffer Analyze
Okta also offers a complete identity Network security solution that organisations can use to manage user access to applications and the associated data. Their MFA solution is adaptive and thus enhances an added layer of protection against compromising events.
The external integration with other tools to the development of the platform enhance the user administration and develops overall security on cloud novelties. Organisations that are committed to Zero Trust architecture would find Okta especially helpful.
Key Features
- Flexy MFA for solitary and superior access security.
- The ability to interface with other cloud-based applications and programs.
- Jim Balsillie stated that strong Zero Trust principles regarding user identity protection shall be in place.
Pros
- Affordable for SMBs
- Intuitive interface
- Strong engagement metrics
Cons
- Limited platform coverage
- Basic listening features
- Lacks advanced analysis
Price: Starts at $50/month
7. Microsoft Defender
Microsoft Defender is an Endpoint detection and response solution that works hand in hand with Microsoft 365. It has enhanced threat hunting, which pinpoint threats and possible attacks before one happens.
Its bringing-together feature within the Microsoft ecosystem guarantee compatibility in the protection of devices and applications. This way it provides the first response and automatically minimizes false positives with the aid of AI, thereby being effective.
Key Features
- To be precise, there are concerns regarding endpoint detection and response (EDR).
- Threat hunting is powered by Artificial Intelligence and the self-executing of actions that need to be taken.
- Consistent with other Microsoft products for one umbrella to protect everything.
Pros
- Integrated with the Windows ecosystem
- Real-time threat detection
- No additional cost for Windows users
Cons
- Limited advanced features
- Performance impact on older systems
- Requires Microsoft ecosystem
Price: Free (Premium plans available with Microsoft 365).
8. Netskope SASE
Netskope SASE provides connectivity with unified security controls as a service for access to cloud applications and data. It avails detailed insight and control of data flow, further enforcing the industry regulations.
The Network security solutions also have smart insights protection measures that give authorized owners protection against insider threats and data leaks. Hybrid work arrangements are where Netskope is most beneficial.
Key Features
- Value added for better compliance and assurance of the flow of data considering privacy and security aspects, which also requires more granular visibility.
- Single point secure access of data and applications in the cloud.
- Smart guarding of data against insiders as well as in cases of a breach.
Pros
- Data-centric security
- Comprehensive cloud visibility
- Unified architecture
Cons
- High upfront cost
- Complex deployment
- Limited legacy app support
Price: Contact for pricing.
9. Darktrace
Darktrace operates with artificial intelligence providing the organization with real-time threat management and eliminating the need for networking expertise. This type learns about the Network protection solutions on its own and is able to recognize patterns of activity that might be associated with an attack.
It is also an advantage since it has the capacity to respond on its own thereby fast acting on threats. Darktrace is an invaluable tool for enterprises that wish to alleviate the workload of many security tasks and build up defences.
Key Features
- Self-protected assessment and prevention of current cyber threats.
- Algorithms to learn without human interaction in order to detect network abnormalities.
- Smart early response to threats without human interference for a quicker response, and defense.
Pros
- Self-learning AI for threat detection
- User-friendly interface
- Works across diverse environments
Cons
- Expensive pricing model
- Requires tuning to reduce false positives
- Limited reporting capabilities
Price: Contact for pricing.
10. CyberArk PAM
 Network Security Solutions
Network Security SolutionsCyberArk PAM is a Privileged Access Network security Management solution. Regarding privileged accounts, CyberArk deals with access rights and takes the account activity into its consideration. It assists organizations in maintaining the concept of least privilege so that insider threats and compromised credentials cannot take full action.
It has session recording and auditing which allows the organization to meet the regulatory requirements of the company. More specifically, the CyberArk is a must-have for companies that work with certain top-secret or other classified information.
Key Features
- Single point of management for privileged accounts in an organisation to enforce the principles of least privilege.
- Record and playback the session for compliance verification.
- Superior prevention techniques against insider threats and credential-propelled threats.
Pros
- Secure privileged access
- Comprehensive audit trails
- Scalable for enterprise use
Cons
- Expensive for small businesses
- Complex implementation
- Steep learning curve
Price: Contact for pricing.
11. JSON NetFlow
JSON NetFlow in particular gives real-time analysis of organizations’ traffic, thus helping them detect a breach in the network. I especially like its ability to set up several customized dashboards for bandwidth tracking, and to notice potential surges in traffic.
Traffic analysis of the specific Network protection solutions platform enables the identification of possible problems such as bottlenecks or weak links in overall network configuration and increase of network protection level. Network administrators or sys admins use it to keep their networks optimum and secure.
Key Features
- Real-time traffic data analysis in contrast to monitoring traffic at different time intervals.
- High-flexible and fully customizable operations in order to facilitate monitoring and analysis.
- Traffic analysis in order to articulate the actual specific weak points to address and enhance traffic flow.
Pros
- Flexible data structure
- Efficient for network monitoring
- Easy integration with tools
Cons
- Requires technical expertise
- Limited visualization tools
- Lack of pre-built solutions
Price: Open-source (Free).
12. Proofpoint Email Protection
 Network Security Solutions
Network Security SolutionsProofpoint helps organizations to guard against email borne threats including phishing, malware and spam. Its AI-based filtering mechanisms guarantee any heavily suspected email is either flagged or blocked from entering the user’s inbox.
It also has data loss prevention (DLP) capabilities that protect any information sent through the email of the Network security solution. As you can see, Proofpoint covers all the aspects of email security to provide a safe and secure connection.
Key Features
- Using Artificial intelligence to block out phishing, malicious and spam emails.
- Some of the security features are based on DLP for safe and respectful correspondence by e-mail.
- A holistic perspective on the email threat spectrum to power next-level email protection.
Pros
- Effective phishing defense
- Advanced malware detection
- Easy integration with email platforms
Cons
- High cost for smaller teams
- Occasional false positives
- Complex initial setup
Price: Starts at $30/user/year.
13. Barracuda Essentials
Barracuda Essentials is the simplest and most comprehensive product on the market that combines email protection against phishing, malware, and spam messages. Its archiving and backup abilities will guarantee e-mail continuity in addition to records recovery after an attack.
The Network security solution application it provides to detect threats is AI-based which means that it prevents new threats before they surface. Most prominently though, Barracuda Essentials would prove most useful to any company that heavily depends on their email communications.
Key Features
- Phishing, malware, as well as spam protection, are combinations that are in multiple layers.
- Clients’ email continuity and recovery functionality provided by the archiving and backup services.
- AI for threat identification to prevent the latest threats to attack and for better security.
Pros
- Comprehensive email security
- Easy-to-use dashboard
- Affordable for SMBs
Cons
- Limited customization
- Basic analytics
- Occasional delays in email filtering
Price: Starts at $2.63/user/month.
14. Lacework Cloud Security
Lacework is known for offering end-to-end cloud security, especially for organizations in multi-cloud environments. Automated monitoring and compliance simplify the use of the cloud by providing security management.
Lacework uses machine learning to be able to address the fluidity, giving the cloud applications optimal protection from these new complex threats. This makes it an ideal solution for industries implementing the cloud model.
Key Features
- Software System for Real-time Cloud Monitoring.
- The flexibility to learn cloud application behaviours and further adapt to them.
- Multi-cloud environment compliance management at its easiest.
Pros
- Real-time monitoring
- Multi-cloud compliance
- Adaptive learning
Cons
- Expensive for startups
- Basic user support
- Complex initial setup
Price: Contact vendor
15. Trend Micro Cloud Security
The Network security solutions include cloud application security, cloud workload protection, and cloud data protection form part of the trend of micro cloud security solutions. Its sophisticated threat intelligence identifies threats and removes malicious programs and ransomware as well as zero-day threats.
The platform is able to sustain compliance of regulatory compliance and offers constant supervision of cloud settings. Trend Micro’s solutions are offered on a flexible scale making it easy for businesses of every size.
Key Features
- Malware identification, ransomware identification, and identification of Zero-day threats.
- Protection of applications, workloads and data through and through across the cloud.
- Ongoing surveillance to conform with the trends poised by various authorities.
Pros
- Broad cloud platform support
- Advanced threat intelligence
- Easy deployment
Cons
- High cost for premium features
- Requires configuration for full efficiency
- Limited third-party integrations
Price: Contact for pricing.
How to Choose the Best Network Security Solutions
- Assess Your Needs: Find out which threats, risks and compliances are most pertinent to your business.
- Evaluate Scalability: Select a Network security tool that allows for future expansion but is not going to take a hit in performance across that expansion process.
- Ease of Integration: It should be adaptive to the current architectures and must complement other application tools.
- Real-Time Monitoring: Choose options that have threat monitoring for 24/7 and alerts as soon as possible.
- Vendor Reputation: Reviews, case studies and industry awards should also be measured to understand the reliability of the sources.
- Cost-Effectiveness: While designing your innovative goods, keep measures such as a balanced budget with other features to guarantee high ROI.
Conclusion
While trying to lay out strategies for the year 2025, one cannot deny the importance that network security plays in organization’s reliability. As cyber threats are increasing at a very high rate, new variants emerging frequently it becomes imperative to be prepared to face such a threat, to prevent such, investing in good security technologies remains unavoidable.
Only if you focus on your organizations’ requirements and analyze the options provided cautiously, can you easily choose one that ensures optimal protection, flexibility and productivity. The 15 top network security solutions provided in this blog post showcase ingenuity, efficiency, and high quality, offering solutions to different business types and industries. Network security is not about protection alone, it is about the freedom to grow your business in the digital space.
FAQs
1. Which kind of network security solutions are widely used today?
The most popular ones are; Firewall, Intrusion prevention systems (IPS), Virtual private networks (VPNs), Endpoint security, multi-factor authentication (MFA), and cloud security solutions. These tools benefit the user; by guarding against such issues as unauthorized access, malware, phishing, and other cyber-related issues.
2. When do I know my business requires a network security solution?
Every company using or storing any type of sensitive information or working in the digital world needs network security software. Any organization responding to customer information and their financial transactions or patented products would benefit from network security as its absence would attract violations and breaches.
3. Application of artificial intelligence to developing modern network security.
Through the use of analytics, artificial intelligence provides real-time protection of the network against threats, probability analysis of threats and programmed responses to threats. It can be used to find abnormalities, eliminate numerous positive results and cope with APTs more efficiently than with the help of classic approaches.
4. Do network security solutions cost a lot of money to put into practice?
Prices depend on the list of the features offered and the solution’s complexity. However, the risk and cost that can be incurred in case of cyber attack is much higher than investing in the safety of the network that supports the business.

